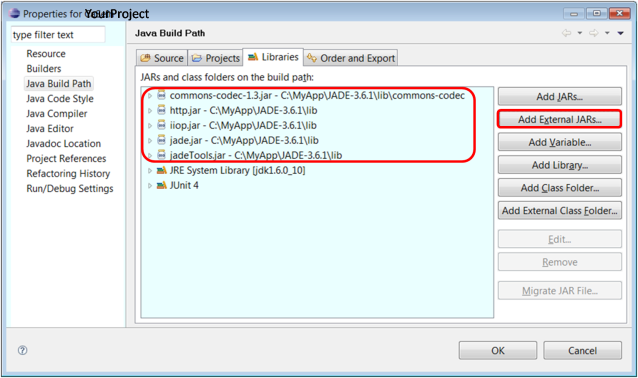
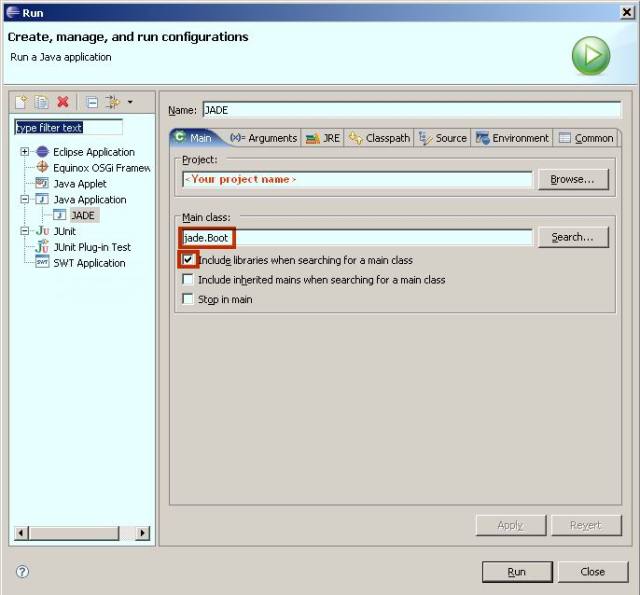
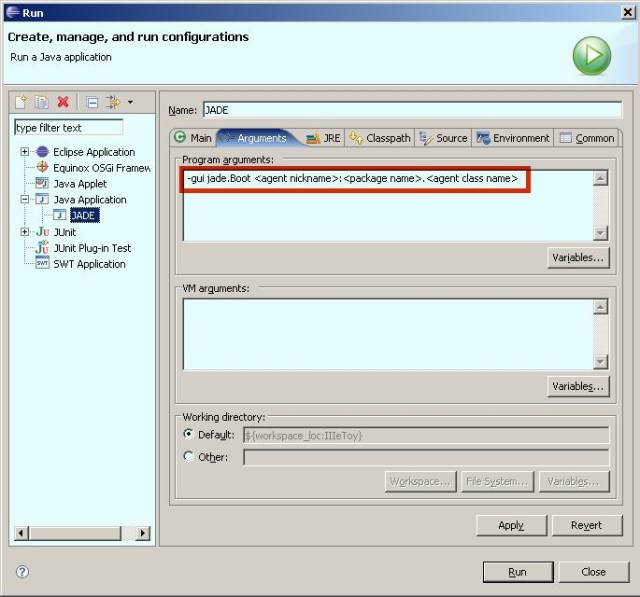
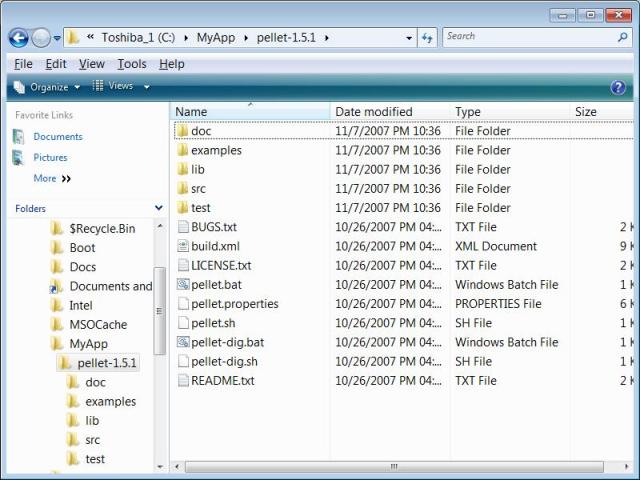
Click  can see my full publication list:
can see my full publication list:
- [PDF] [BibTeX] Wan-rong Jih, Chi-Chia Huang, and Jane Yung-jen Hsu. Context life cycle management in smart space environments. In ICPS09 Workshop on Agent-Oriented Software Engineering Challenges for Ubiquitous and Pervasive Computing (AUPC2009), London, UK, July 2009.
- [PDF] [BibTeX] Wan-rong Jih and Jane Yung-jen Hsu. Agent-based Ubiquitous Computing, volume 1 of Atlantis Ambient and Pervasive Intelligence, chapter Agent-Based Context-Aware Service in a Smart Space, pages 131 – 146. Atlantis Press, June 2009.
- [PDF] [BibTeX] Wan-rong Jih, Jane Yung-jen Hsu, Han-Wen Chang, and Umi Laili Yuhana. Agent-based context consistency management in smart space environments. In AAMAS-09 Workshop on Service-Oriented Computing and Agent-Based Engineering (SOCASE’2009), WS05, Budapest, Hungary, May 2009.
- [PDF] [BibTeX] Umi Laili Yuhana, Li-lu Chen, Jane Yung-jen Hsu, and Wan-rong Jih. An ontology based approach for searching neighborhood building. In Proceedings of The Third International Seminar Information and Communication Technology Seminar (ICTS07), pages 106 – 112, Surabaya, Indonesia, September 2007.
- [PDF] [BibTeX] Wan-rong Jih, Jane Yung-jen Hsu, Tsu-Chang Lee, and Li-lu Chen. A multi-agent contextaware service platform in a smart space. Journal of Computers, 18(1):45–60, April 2007.
- [PDF] [BibTeX] Wan-rong Jih, Li-lu Chen, and Jane Yung-jen Hsu. Context-aware service platform in a smart space. In AAMAS-07 Workshop on Agent-Based Ubiquitous Computing (ABUC2007), WS2, Honolulu, Hawaii, USA, May 2007. [acceptance:25%, Best Paper Award].
- [PDF] [BibTeX]Jane Yung-jen Hsu, Kwei-Jay Lin, Tsung-Hsiang Chang, Chien-ju Ho, Han-Shen Huang, and Wan-rong Jih. Parameter learning of personalized trust models in broker-based distributed trust management. Information Systems Frontiers: Special Issue on Web and Distributed Information Systems, 8(4):321–333, September 2006. Springer .
- [PDF] [BibTeX] Wan-rong Jih, Jane Yung-jen Hsu Hsu, and Tse-Ming Tsai. Context-aware service integration for elderly care in a smart environment. In AAAI 2006 Workshop: Modeling and Retrieval of Context Retrieval of Context, pages 44– 48, Boston, Massachusetts, USA, July 2006.
- [PDF] [BibTeX] Wan-rong Jih, Jane Yung-jen Hsu, Chao-Lin Wu, Chun-Feng Liao, and Shao-you Cheng. A multi-agent service framework for context-aware elder care. In AAMAS-06 Workshop on Service-Oriented Computing and Agent-Based Engineering (SOCABE’2006), WS18, pages 61– 75, Future University, Hakodate, Hokkaido, Japan, May 2006.
- [PDF] [BibTeX] Shao-you Cheng, Wan-rong Jih, and Jane Yung-jen Hsu. Context-aware policy matching in event-driven architecture. In AAAI 2005 Workshop: Contexts and Ontologies: Theory, Practice and Applications, pages 140 – 141, Pittsburgh, Pennsylvania, USA, July 2005.
- [PDF] [BibTeX] Wan-rong Jih, Shao-youg Cheng, and Jane Yung-jen Hsu. Context-aware access control on pervasive healthcare. In EEE’05 Workshop: Mobility, Agents, and Mobile Services (MAM), pages 21– 28, Hong Kong, March 2005.
- [PDF] [BibTeX] Wan-rong Jih and Jane Yung-jen Hsu. A family competition genetic algorithm for the pickup and delivery problems with time window. Bulletin of the College of Engineering, 90:121–130, 2004.This original PDF contains Chinese abstract, here is an English-only version PDF.
- [PDF] [BibTeX] Wan-rong Jih, Cheng-yen Kao, and Jane Yung-jen Hsu. Using family competition genetic algorithm in pickup and delivery problem with time window constraints. In Proceedings of the 2002 IEEE International Symposium on Intelligent Control, pages 496–501, Vancouver, British Columbia, Canada, October 2002.
- [PDF] [BibTeX] Wan-rong Jih and Jane Yung-jen Hsu. Dynamic vehicle routing using hybrid genetic algorithms. In Proceedings of the 1999 IEEE International Conference on Robotics & Automation, pages 453–458, 1999.
- [PDF] [BibTeX] Wan-rong Jih, Ying-Ping Chen, and Jane Yung-jen Hsu. A comparative study of genetic algorithms for vehicle routing with time constraints. In Proceedings of the 1996 International Computer Symposium, pages 17–24, 1996.